Although they come bundled with an anti-theft system, Samsung phones apparently include a vulnerability that nullifies that feature.
It has already been a few years since Apple phones and many Android phones, under certain conditions, are stolen for nothing. The reason for that phenomenon is related to a software protection that manifests itself by requiring the former user account and the related password to reset the terminal even after a general reset and deletion of all data.
Although no solution has been found for iCloud to bypass activation lock, if you have a Samsung smartphone the whole process seems to be surprisingly simple. The only slightly weirder thing you need is a USB stick with a microUSB port on one end to plug directly into your phone. However, the latter are quite easy to find these days.
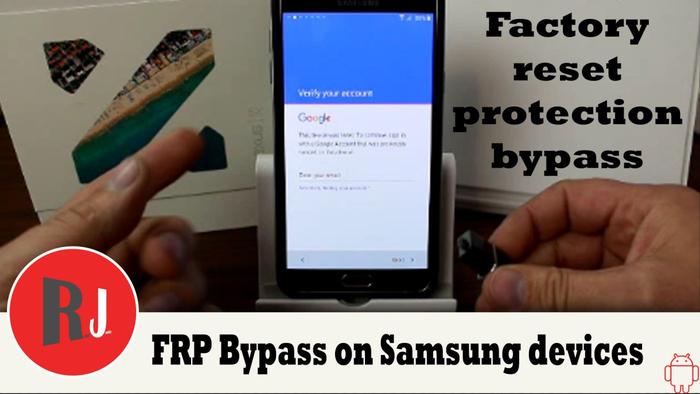
The tutorial above is made by a netizen with the nickname RootJunky and it only works on Samsung smartphones, it was demonstrated on a Galaxy Note 5. So if you own a Nexus, for example, you're safe. The cycle of executed actions is quite simple. The phone is put into recovery mode and data deletion is initiated. When you try to activate the phone again and you are asked for the email address that was previously associated with the device, connect the stick with a file that you find in the description of the YouTube clip and a window will automatically appear through which you can run it. That program will give you access to your smartphone's setup menu through which you can initialize a new master reset. The difference is that this time you will be able to use a new Google account to activate the phone or, if you want, you can initialize the gadget without any account at all.
It remains to be seen if the same serious vulnerability exists on other Android smartphones.
